
Service Portfolio
Comprehensive cybersecurity consultancy, Intelligence Services and and trainings to safeguard organizations.
Information Security Consulting
Our certified ISO 27001 managers, auditors and experts in the field we will help you with:
Setting up and maintaining your Informations Security Management System
Conducting Audits and GAP Analysis
The right policies and compliance achivement
ISO/IEC 27001:2013 to ISO/IEC 27001:2022 transition
Risk Assessments
Training your stuff
and more..
Consultancy services are offered remotely to our clients world wide. Initial meetings in person are possible.

Penetration Testing
With our penetration testing service we offer a complete range of assessments, from Black Box to Grey Box to White Box testing. This includes web application testing via OWASP standards, OT security assessments, and Red Teaming operations to ensure your systems are thoroughly tested and secured. We identify sophisticated vulnerabilities before they can be exploited by malicious actors.
Thanks to our Elite Hackers network, for highly sophisticated projects we are able to provide a team of elite ethical hackers with deep expertise and highest offensive security certificates in short time.
What we offer:
Comprehensive Penetration Testing: Includes Black Box, Grey Box, and White Box testing to evaluate your system's security from different angles.
OWASP Security: Testing based on OWASP standards to protect against common and critical web application vulnerabilities.
OT Security: Specialized testing for operational technology environments, ensuring that your critical infrastructure is secure.
Red Teaming: Simulated cyber-attacks that mimic real-world threats to test your organization's defense mechanisms.
Elite Ethical Hacker Team: Highly skilled professionals equipped to tackle the most complex security challenges.

OSINT (OPEN SOURCE INTELLIGENCE)
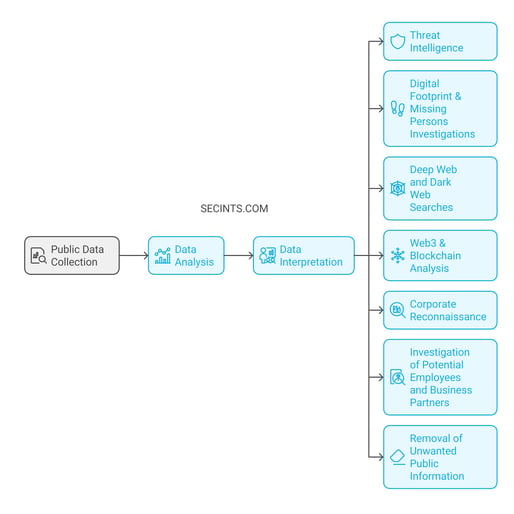
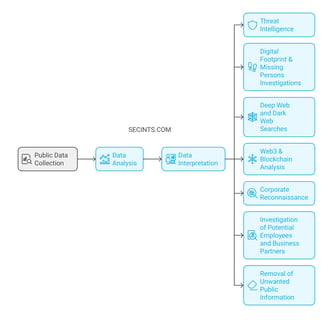
In today's information-rich world, vast amounts of public data are waiting to be uncovered and transformed into actionable insights. With information comes power, and our OSINT services are designed to empower you by extracting, analyzing, and interpreting publicly available data, delivering crucial intelligence tailored to your specific needs. Whether you're navigating corporate security, conducting private investigations, or researching market trends, we provide the knowledge to help you make informed decisions.
Our services include:
Threat intelligence: Stay ahead of cyber threats with advanced monitoring and analysis to protect your digital infrastructure.
Digital footprint & missing persons investigations: We leverage open-source data, social media, and digital forensics to trace online activities and assist in finding missing persons.
Deep web and dark web searches: Access critical information hidden below the surface of the internet to uncover risks, fraud, and illicit activities.
Web3 & blockchain analysis: From cryptocurrency transactions to decentralized platforms, we analyze blockchain data to track money flows, money laundering, scams & suspicious activities.
Corporate reconnaissance: We gather publicly accessible information about companies, including their email addresses, servers, employee details, and other technical infrastructure. This intelligence allows us to identify security weaknesses and vulnerabilities, laying the foundation for advanced services like penetration testing, social engineering and security audits.
Investigation of potential employees and business partners: Gather critical information about individuals or organizations before making business or hiring decisions, ensuring you're partnering with trustworthy and credible entities.
Finding and removing unwanted public information about individuals: We help you track and remove unwanted or sensitive personal information from public sources, protecting your privacy and reputation.
Related Intelligence Disciplines:
GEOINT (Geospatial Intelligence): produced through a combination of imagery intelligence (IMINT) and geospatial information.
HUMINT (Human Intelligence): Derived from human sources. One of the oldest forms of data collection. The public perception of this discipline is usually related to clandestine activities – think undercover missions and spies. Yet, the reality is that most of the sources used these days are less exciting and much more overt in nature. In fact, most of the raw information used to produce this intelligence is collected through interviews conducted with witnesses, suspects, and Persons Of Interest in an investigation, for example.
SIGINT (Signals Intelligence): Produces from the interception an dexploitation of signals.
Our OSINT services combine state-of-the-art tools, methodologies, and industry expertise to offer unparalleled insights. From tracing digital footprints to uncovering hidden technical information about organizations, we provide timely, relevant, and impactful intelligence that strengthens your decision-making.
Unlock the potential of public data with our OSINT solutions—because in today’s digital age, information is your greatest asset. Contact us today to learn more.




Social Engineering
The Art of Human Hacking
Social Engineering Services: The Next Level of Security Testing with AI
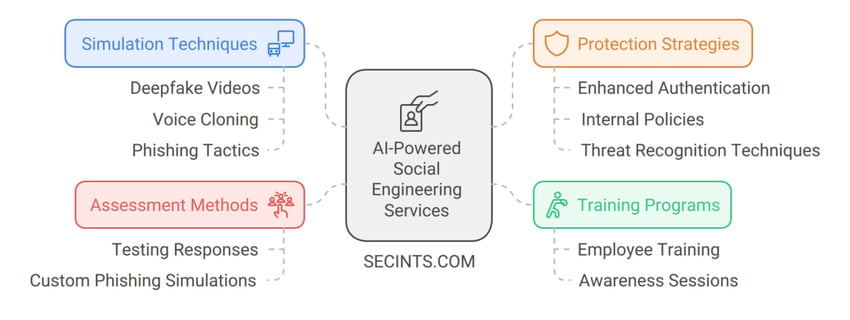
Leverage cutting-edge AI-powered social engineering techniques to test and strengthen your company’s defenses. From deepfake simulations to voice cloning and advanced phishing tactics, we ensure your team is ready to recognize and counter even the most sophisticated attacks.
Overview:
Social engineering attacks are evolving, and so should your defenses. At the intersection of psychology and technology, our next-level social engineering services use AI to simulate real-world attacks that exploit human vulnerabilities.
While firewalls, encryption and security protocols are essential, humans remain the weakest link in any security chain. No matter how advanced your defences, if your employees fall for phishing attempts, voice cloning, or deepfake scams, your entire organization is at risk.
With AI, we replicate highly convincing attacks designed to deceive even the most vigilant employees. From creating deepfake videos that mimic real executives to using voice cloning to imitate familiar voices over the phone, we employ cutting-edge techniques to assess your company's preparedness against today’s most advanced threats.
Ultimately, no security measure or firewall can fully protect you if people don't act with caution and awareness. That's why we focus on testing and training your employees to recognize and respond to social engineering attacks, ensuring that your human defences are just as strong as your technical ones.
Our services include:
AI-driven social engineering simulations: Test your employees with realistic phishing emails, deepfake videos, and voice cloned calls, showing how susceptible your organization is to modern threats. See how employees react when faced with convincing fake videos and audio.
Phishing & spear phishing campaigns: We create customized AI-enhanced phishing simulations to test how effectively your employees can identify and respond to targeted attacks.
Training and awareness programs: After testing, we provide comprehensive training sessions to help your employees recognize social engineering threats and understand how to respond quickly and effectively.
Protection strategies and recognition techniques: We don’t just expose weaknesses - we help you build resilience. Our solutions include proactive strategies to protect against AI-driven social engineering attacks, such as enhanced authentication methods, internal policies, and threat recognition techniques.
Our AI-powered social engineering services provide the ultimate stress test for your organization. By simulating the most sophisticated attacks in a safe environment, we help you identify vulnerabilities and teach your team how to recognize and counter these tactics before real-world threats strike.
Prepare for the future of cybercrime with our AI-enhanced social engineering solutions. Contact us today to fortify your organization and outsmart even the most advanced attackers.

Contact Us
Reach out to SΞCINTS today for expert cybersecurity consulting, services, and training solutions for your business.
+43 690 10 44 0002
